Creating and Managing Groups
By default, only an Administrator can perform the tasks described in the following topics. An Administrator can enable other users to perform these tasks by assigning specific system security roles. See Requirements.
In this topic:
Requirements
To let non-Administrators create and manage users and groups, grant them group-based access to the required security roles.
-
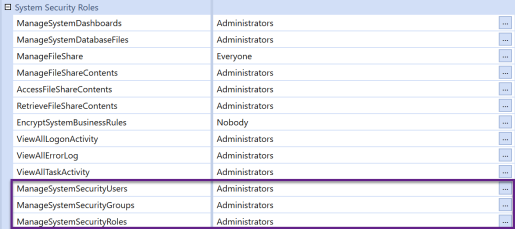
Click System > Security > System Security Roles.
-
Click Edit by these roles to assign the group in which the user is a member:
-
ManageSystemSecurityUsers: Assignees can create, modify and mange users.
-
ManageSystemSecurityGroups: Assignees can define, modify and mange groups.
-
ManageSystemSecurityRoles: Assignees can manage roles to provide group-based, functionally-tailored access to artifacts and tools.
-
To revoke the ability to manage users, groups and roles, remove assignees from the relevant role. See Manage System Security.
About Groups and Inherited Security
You cannot assign individual users access to tools and artifacts. System security roles (roles) to which you assign groups determine this access. Create groups to grant large numbers of users or other groups the functionally-tailored access that they require.
You can define nested, hierarchical groups to best suit your organizational entities, workflows and reporting structures. Nested groups contain lower-level child groups. In this case, child groups - and the users that they contain - inherit the access defined for the parent group.
NOTE: Groups cannot be externally authenticated.
About Exclusion Groups
Use exclusion groups to grant almost everyone - except a particular group or a small number of users - access to a tool or artifact. For example, if everyone but Jim Fey and Lee Diaz must create dashboards, define an exclusion group in which Jim and Lee are members set to "Deny Access". All other members are set to "Allow Access". To easily grant access to dashboards, assign the exclusion to which gives everyone access except Lee and Jim access.
Because groups providing access to data and artifacts may contain many groups, removing just a few users - to reflect a corporate reorganization for example, from the group hierarchy can be time consuming. To handle the reorganization, create an exclusion group with the users involved and apply it to the roles they no longer need.
Tips and Best Practices
-
The Administrator is assigned to all roles, so they can always manage artifacts, data and tools. Assigning other groups to security roles does not revoke the Administrator's access.
-
Child groups, nested in higher-level parent groups, can access the tools and artifact that the parent group can, given the parent group's assignment to system security roles (roles). This access is inherited in group hierarchies, from a parent level downward to child groups.
-
Removing child groups from parent groups revokes access to the tools and artifacts that the parent group provides, based on its assignments to roles.
-
In an exclusion group, access to artifacts is determined based on the exclusion order you specify, regardless of a user's membership in a group. To ensure that users who are in several groups can not access artifacts but everyone else can, put:
-
The groups to which the users belong at the top, set to "Allow Access".
-
The individual users below the groups and set the users to "Deny Access".
-